Corporate Governance
By enhancing transparency, accountability, and efficiency, strengthen the balance between management and shareholders, establish effective risk management and internal control mechanisms, to enhance long-term corporate value and promote sustainable operations.
Menu
Information Security
Information Security Objectives
- Protect the security of the company’s business services, ensuring that information is only accessible by authorized personnel, in order to safeguard customer interests, maintain customer data, and ensure its confidentiality.
- Protect the security of the company’s business services, preventing unauthorized modifications, to ensure their accuracy and integrity.
- Establish the company’s information security continuity plan to ensure the continuous operation of the company’s business services.
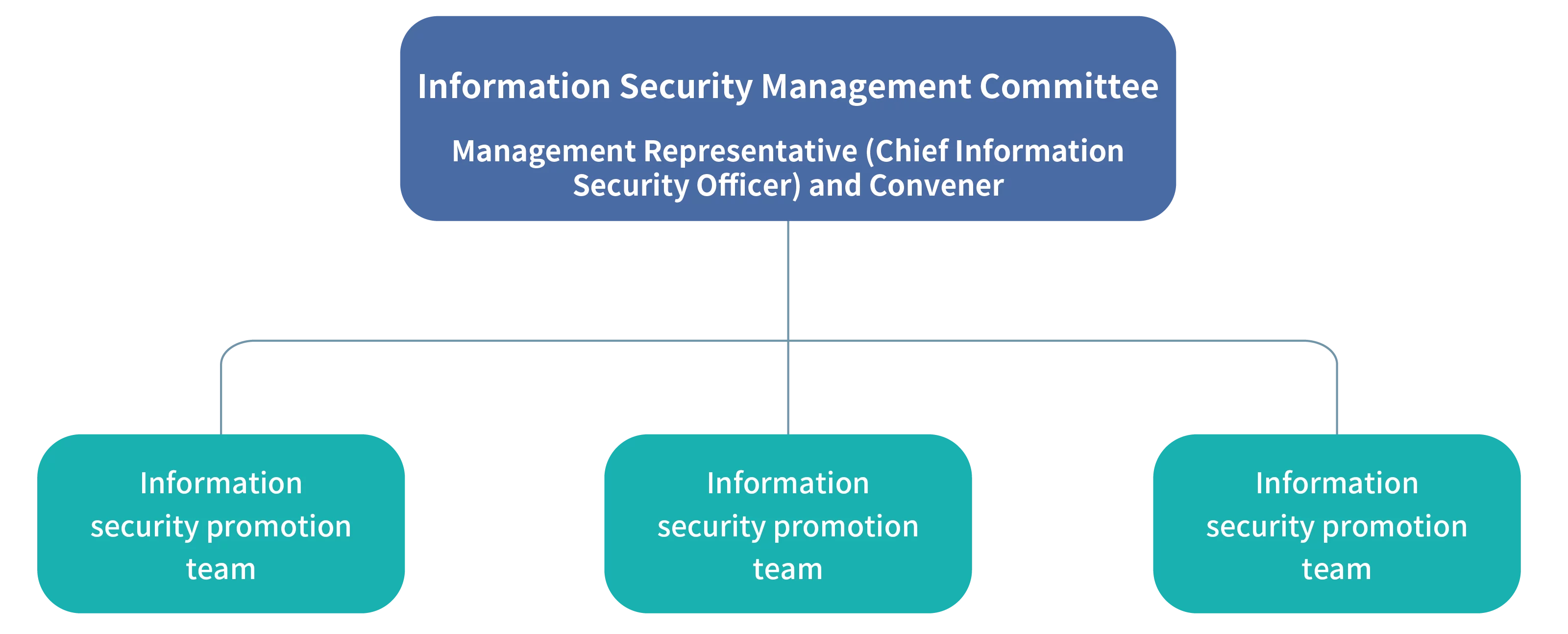
Information Security Management Committee
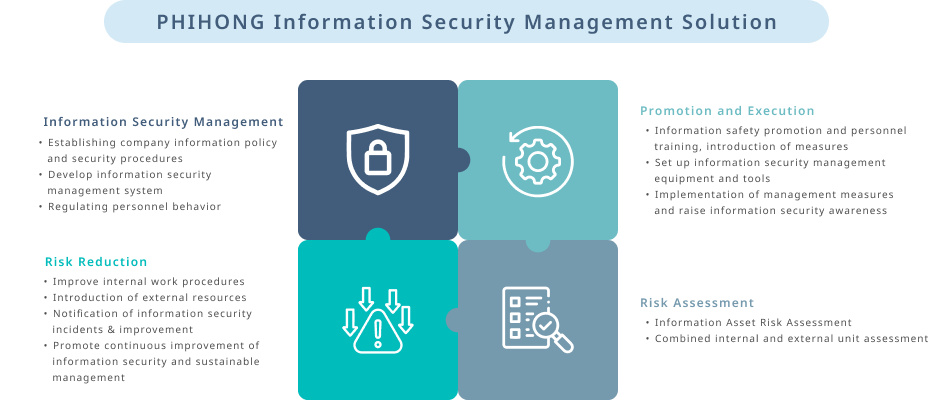
Information Security Management Measures
| Category | Management Measures | Implementation Status in 2023 |
| Privilege Management | Personnel account, authorization management and system operation behavior management measures | Internal personnel account access management and auditing |
| Access Control | Control measures for personnel access to internal and external systems and data transmission channels | • Internal/external access control measures • Data leakage control measures • Operation behavior track record analysis |
| External Threats | Internal System Vulnerabilities, Infection Channels, and Protection Measures | Host/Computer Vulnerability Detection nd Updates Virus Protection and Malware Detection |
| Vulnerability Scanning | Scanning for vulnerabilities in PC and server systems, followed by improvement and continuous tracking of identified weaknesses, aims to detect potential information security threats and vulnerabilities early, thereby enhancing operational and protective capabilities in information security. | Regular drills |
| Education & Training | Regularly educating users and colleagues on information security concepts. | Regular drills |
| Social Engineering Drill | To raise awareness among colleagues regarding email security and prevent potential network security risks and personal data breaches resulting from malicious email browsing, Phihong conducts at least two email social engineering drills annually | Regular drills |